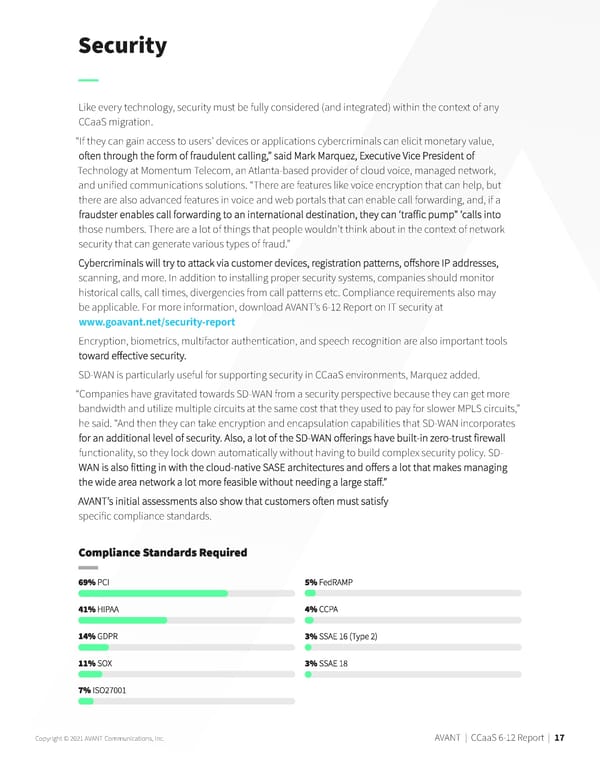
Security Like every technology, security must be fully considered (and integrated) within the context of any CCaaS migration. “If they can gain access to users’ devices or applications cybercriminals can elicit monetary value, Technology at Momentum Telecom, an Atlanta-based provider of cloud voice, managed network, and unified communications solutions. “There are features like voice encryption that can help, but there are also advanced features in voice and web portals that can enable call forwarding, and, if a those numbers. There are a lot of things that people wouldn’t think about in the context of network security that can generate various types of fraud.” scanning, and more. In addition to installing proper security systems, companies should monitor historical calls, call times, divergencies from call patterns etc. Compliance requirements also may be applicable. For more information, download AVANT’s 6-12 Report on IT security at www.goavant.net/security-report. Encryption, biometrics, multifactor authentication, and speech recognition are also important tools SD-WAN is particularly useful for supporting security in CCaaS environments, Marquez added. “Companies have gravitated towards SD-WAN from a security perspective because they can get more bandwidth and utilize multiple circuits at the same cost that they used to pay for slower MPLS circuits,” he said. “And then they can take encryption and encapsulation capabilities that SD-WAN incorporates functionality, so they lock down automatically without having to build complex security policy. SD- specific compliance standards. Copyright © 2021 AVANT Communications, Inc. AVANT | CCaaS 6-12 Report | 17
 CCaaS Report with trends and research Page 16 Page 18
CCaaS Report with trends and research Page 16 Page 18