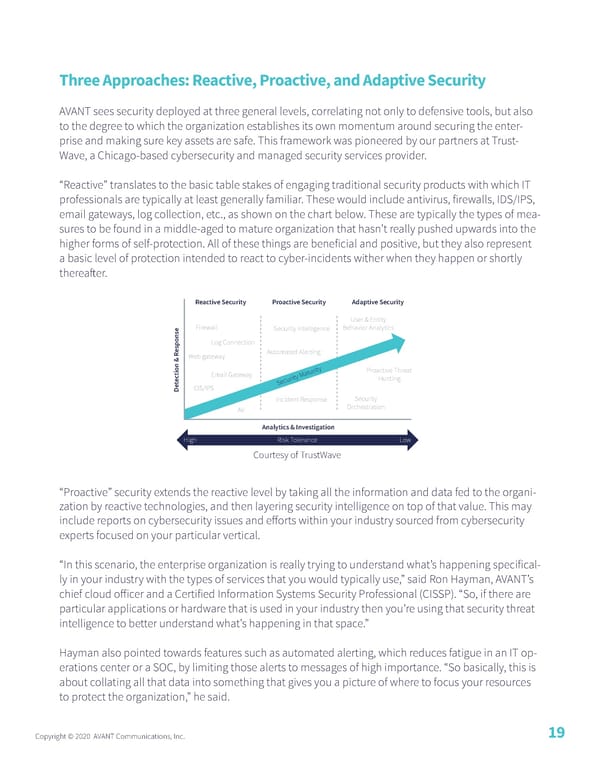
Three Approaches: Reactive, Proactive, and Adaptive Security AVANT sees security deployed at three general levels, correlating not only to defensive tools, but also to the degree to which the organization establishes its own momentum around securing the enter- prise and making sure key assets are safe. This framework was pioneered by our partners at Trust- Wave, a Chicago-based cybersecurity and managed security services provider. “Reactive” translates to the basic table stakes of engaging traditional security products with which IT professionals are typically at least generally familiar. These would include antivirus, firewalls, IDS/IPS, email gateways, log collection, etc., as shown on the chart below. These are typically the types of mea- sures to be found in a middle-aged to mature organization that hasn’t really pushed upwards into the higher forms of self-protection. All of these things are beneficial and positive, but they also represent a basic level of protection intended to react to cyber-incidents wither when they happen or shortly thereafter. Reactive Security Proactive Security Adaptive Security User & Entity Firewall Security Intelligence Behavior Analytics esponse Log Connection Web gateway Automated Alerting tion & R Email Gateway turity Proactive Threat ec Hunting t Security Ma De IDS/IPS Incident Response Security AV Orchestration Analytics & Investigation High Risk Tolerance Low Courtesy of TrustWave “Proactive” security extends the reactive level by taking all the information and data fed to the organi- zation by reactive technologies, and then layering security intelligence on top of that value. This may include reports on cybersecurity issues and efforts within your industry sourced from cybersecurity experts focused on your particular vertical. “In this scenario, the enterprise organization is really trying to understand what’s happening specifical- ly in your industry with the types of services that you would typically use,” said Ron Hayman, AVANT’s chief cloud officer and a Certified Information Systems Security Professional (CISSP). “So, if there are particular applications or hardware that is used in your industry then you’re using that security threat intelligence to better understand what’s happening in that space.” Hayman also pointed towards features such as automated alerting, which reduces fatigue in an IT op- erations center or a SOC, by limiting those alerts to messages of high importance. “So basically, this is about collating all that data into something that gives you a picture of where to focus your resources to protect the organization,” he said. Copyright © 2020 AVANT Communications, Inc. 19
 Managed Security Trends and Insights Page 19 Page 21
Managed Security Trends and Insights Page 19 Page 21