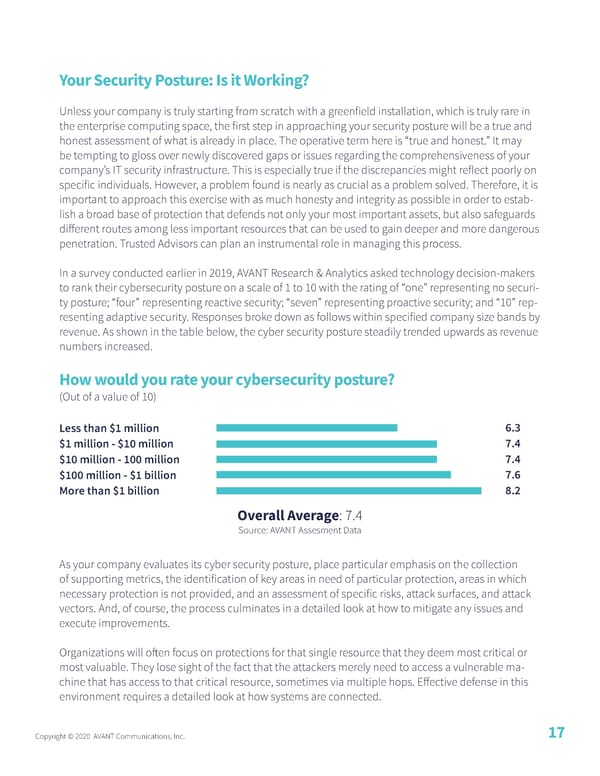
Your Security Posture: Is it Working? Unless your company is truly starting from scratch with a greenfield installation, which is truly rare in the enterprise computing space, the first step in approaching your security posture will be a true and honest assessment of what is already in place. The operative term here is “true and honest.” It may be tempting to gloss over newly discovered gaps or issues regarding the comprehensiveness of your company’s IT security infrastructure. This is especially true if the discrepancies might reflect poorly on specific individuals. However, a problem found is nearly as crucial as a problem solved. Therefore, it is important to approach this exercise with as much honesty and integrity as possible in order to estab- lish a broad base of protection that defends not only your most important assets, but also safeguards different routes among less important resources that can be used to gain deeper and more dangerous penetration. Trusted Advisors can plan an instrumental role in managing this process. In a survey conducted earlier in 2019, AVANT Research & Analytics asked technology decision-makers to rank their cybersecurity posture on a scale of 1 to 10 with the rating of “one” representing no securi- ty posture; “four” representing reactive security; “seven” representing proactive security; and “10” rep- resenting adaptive security. Responses broke down as follows within specified company size bands by revenue. As shown in the table below, the cyber security posture steadily trended upwards as revenue numbers increased. How would you rate your cybersecurity posture? (Out of a value of 10) Less than $1 million 6.3 $1 million - $10 million 7.4 $10 million - 100 million 7.4 $100 million - $1 billion 7.6 More than $1 billion 8.2 Overall Average: 7.4 Source: AVANT Assesment Data As your company evaluates its cyber security posture, place particular emphasis on the collection of supporting metrics, the identification of key areas in need of particular protection, areas in which necessary protection is not provided, and an assessment of specific risks, attack surfaces, and attack vectors. And, of course, the process culminates in a detailed look at how to mitigate any issues and execute improvements. Organizations will often focus on protections for that single resource that they deem most critical or most valuable. They lose sight of the fact that the attackers merely need to access a vulnerable ma- chine that has access to that critical resource, sometimes via multiple hops. Effective defense in this environment requires a detailed look at how systems are connected. Copyright © 2020 AVANT Communications, Inc. 17
 Managed Security Trends and Insights Page 17 Page 19
Managed Security Trends and Insights Page 17 Page 19