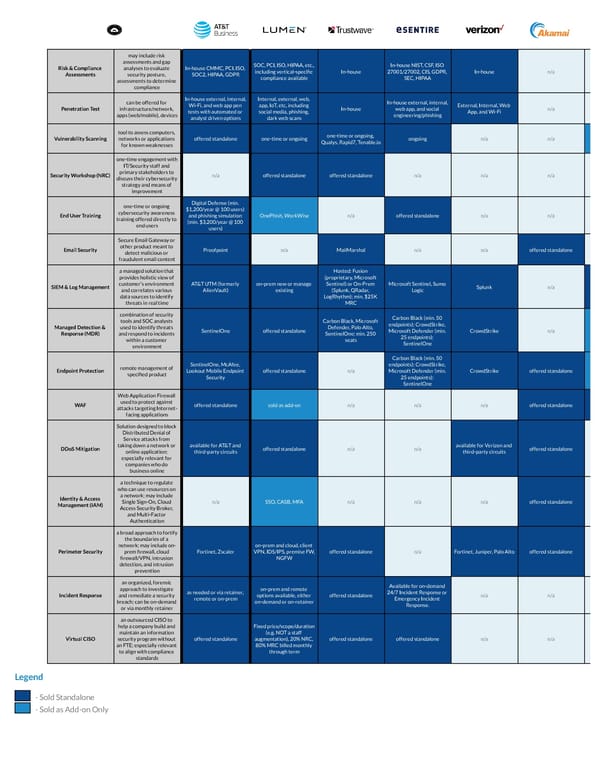
may include risk assessments and gap SOC, PCI, ISO, HIPAA, etc., In-house NIST, CSF, ISO Risk & Compliance analyses to evaluate In-house CMMC, PCI, ISO, including vertical-specic In-house 27001/27002, CIS, GDPR, In-house n/a Assessments security posture, SOC2, HIPAA, GDPR compliance available SEC, HIPAA assessments to determine compliance In-house external, internal, Internal, external, web, can be offered for In-house external, internal, Wi-Fi, and web app pen app, IoT, etc, including External, Internal, Web Penetration Test infrastructure/network, In-house web app, and social n/a tests with automated or social media, phishing, App, and Wi-Fi apps (web/mobile), devices engineering/phishing analyst driven options dark web scans tool to assess computers, one-time or ongoing, Vulnerability Scanning networks or applications offered standalone one-time or ongoing ongoing n/a n/a Qualys, Rapid7, Tenable.io for known weaknesses one-time engagement with IT/Security staff and primary stakeholders to Security Workshop (NRC) n/a offered standalone offered standalone n/a n/a n/a discuss their cybersecurity strategy and means of improvement Digital Defense (min. one-time or ongoing $1,200/year @ 100 users) cybersecurity awareness End User Training and phishing simulation OnePhish, WorkWise n/a offered standalone n/a n/a training offered directly to (min. $3,200/year @ 100 end users users) Secure Email Gateway or other product meant to Email Security Proofpoint n/a MailMarshal n/a n/a offered standalone detect malicious or fraudulent email content a managed solution that Hosted: Fusion provides holistic view of (proprietary, Microsoft customer’s environment AT&T UTM (formerly on-prem new or manage Sentinel) or On-Prem Microsoft Sentinel, Sumo SIEM & Log Management Splunk n/a and correlates various AlienVault) existing (Splunk, QRadar, Logic data sources to identify LogRhythm); min. $25K threats in real time MRC combination of security Carbon Black (min. 50 tools and SOC analysts Carbon Black, Microsoft endpoints); CrowdStrike, Managed Detection & used to identify threats Defender, Palo Alto, SentinelOne offered standalone Microsoft Defender (min. CrowdStrike n/a Response (MDR) and respond to incidents SentinelOne; min. 250 25 endpoints); within a customer seats SentinelOne environment Carbon Black (min. 50 SentinelOne, McAfee, endpoints); CrowdStrike, remote management of Endpoint Protection Lookout Mobile Endpoint offered standalone n/a Microsoft Defender (min. CrowdStrike offered standalone specied product Security 25 endpoints); SentinelOne Web Application Firewall used to protect against WAF offered standalone sold as add-on n/a n/a n/a offered standalone attacks targeting Internet- facing applications Solution designed to block Distributed Denial of Service attacks from taking down a network or available for AT&T and available for Verizon and DDoS Mitigation offered standalone n/a n/a offered standalone online application; third-party circuits third-party circuits especially relevant for companies who do business online a technique to regulate who can use resources on a network; may include Identity & Access Single Sign-On, Cloud n/a SSO, CASB, MFA n/a n/a n/a offered standalone Management (IAM) Access Security Broker, and Multi-Factor Authentication a broad approach to fortify the boundaries of a network; may include on- on-prem and cloud, client Perimeter Security prem rewall, cloud Fortinet, Zscaler VPN, IDS/IPS, premise FW, offered standalone n/a Fortinet, Juniper, Palo Alto offered standalone rewall/VPN, intrusion NGFW detection, and intrusion prevention an organized, forensic Available for on-demand approach to investigate on-prem and remote as needed or via retainer, 24/7 Incident Response or Incident Response and remediate a security options available, either offered standalone n/a n/a remote or on-prem Emergency Incident breach; can be on-demand on-demand or on-retainer Response. or via monthly retainer an outsourced CISO to help a company build and Fixed price/scope/duration maintain an information (e.g. NOT a staff Virtual CISO security program without offered standalone augmentation), 20% NRC, offered standalone offered standalone n/a n/a an FTE; especially relevant 80% MRC billed monthly to align with compliance through term standards Legend - Sold Standalone - Sold as Add-on Only
 Top Cybersecurity vendors 2023 Page 1
Top Cybersecurity vendors 2023 Page 1 