Security Matrix
Security Matrix Provider link to provider's 11:11 Systems Ntirety Trustwave Cloudflare eSentire Nord Security Console Connect by Thrive Pathfinder (formerly Green PCCWr profile Cloud Defense & iland) Primary Line main service the Cloud & MSSP Cloud & Managed MSSP DDoS, WAF, & MSSP Data Encryption, Carrier MSP & MSSP of Business provider offers Service Provider ZTNA Password Management, VPN, ZTNA Year year founded 2011 1998 1995 2009 2001 2012 2005 2000 Company Established # Employees number of in- 350 450 2,000 2,500 475 1,200 1,000 350 house employees Elevator Pitch provider's value Green Cloud With 20+ years of Focused on threat Scale - Anycast Within 35 Cloud-based PCCW Global's 250 prop Defense is a experience, detection and network with seconds eSentire cybersecurity cybersecurity experienced Channel ONLY Ntirety embeds response, 200+ global starts tools for consultants can engineers craft MSSP & Cloud compliant security Trustwave is a data centers investigating, business of improve customers’ and deliver the Provider. We throughout your IT leading and 37 Tbps isolating, and every size. business processes right solutions specialize in and company cybersecurity and capacity containing NordLayer for and operations at to maximize helping partners culture. Protect managed security suspicious VPN, SASE & every step ROI. Industry- secure their the entirety of services company Collective activity, typically ZTNA. NordPass according to best leading, customers your enterprise offering a Intelligence - resolved in under for password practices, automated, self networks from through a comprehensive We support 17 minutes. Our management. compliances, and service attackers. comprehensive portfolio of over 26M+ web core belief is it is NordLocker for certifications with platform back Whether our pre- compliant security managed security applications our duty to data encryption. services including by ServiceNow sales resources solution from a services, security RESPOND and A simple path to advisory and delivers optimal are leading single testing, consulting Ease of Use - STOP threats fundamental assessment, client discovery or just relationship. and professional Changes without paying security and architecture, experience. backing up our services, and data deploy w/in 30 extra. Founded in application implementation, and partner personnel, protection seconds 2001 we started access controls customization. We ensure we have the technology. globally the MDR category to users. clients and solutions, tools and protect over Due to its partners have and people in Infrastructure $6 trillion in international access to the place to help Agnostic - We assets. knowledge and latest cloud advisors success support on- experience in the technologies, in the security prem, hybrid, cybersecurity arena, cyber-security space. and multi-cloud PCCW Global best practices, supports and helps networking Integrated the customers solutions, and Solution - All address the compliance data centers complexity and assistance. provide the scale of IT same feature environments, which set creates multiple points of
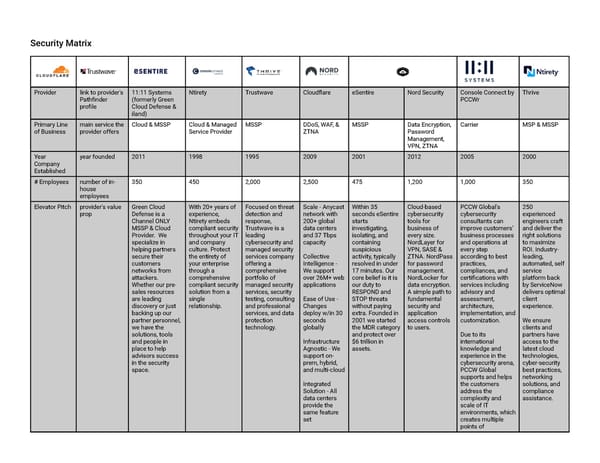
vulnerability – both internally and externally, as well as meeting regulatory and compliance management challenges. PCCW Global follows the Managed Security Services business model proposing Security Services and solutions which helps customers reduce business risk, preserve existing investments, and improve cybersecurity defences. PCCW Global’s solution portfolio is supported from a highly skilled GSOC and 24/7 SOC support team. The solutions follow the Managed Security Services business model and ‘Pay as you Grow’ concept based on a monthly fee subscription. # Years how long the 10 20 25 12 20 10 10 5 Offered offering has been available to customers Industry- Gartner, - - Gartner MQ 2021 Forrester IDC MarketScape - - - Ranked Forrester, or Managed Security Wave for DDoS US MDR 2021 similar industry Services 2019 Mitigation Leader rankings (retired) Leader Solutions achieved in the (Leader) cybersecurity Forrester Wave market MSSP Q3 2020 2021 Forrester Leader New Wave for Edge
Development Platforms (Leader) 2021 Forrester New Wave for ZTNA (Contender) 2021 Gartner Magic Quadrant for Web Application Firewall (Challenger) # Security number of 300 500 200,000 confidential confidential confidential 300 300 Customers customers the company has that are specifically consuming cybersecurity services Minimum what is the - $500 - - - - $500 $3,000 MRC for minimum deal Ongoing size you will Security consider for an ongoing security opportunity (i.e. MRC, managed services)? Minimum what is the $1,250 $1,800 - - - - $800 $15,000 NRC for One- minimum deal Time Security size you will consider for a one-time security opportunity (i.e. NRC, professional services)? Security attributes of In-house/3rd party In-house; In-house; In-house; In-house; - In-house; 24/7/365; In-house; Operations provider's hybrid; 24/7/365, 24/7/365; 3 24/7/365; 9 24/7/365; 4 24/7/365; 2 1 Location; 12 SOC 24/7/365; 3 Center (SOC) SOC(s) 2 Locations; 30 Locations; 35 SOC Locations; 300 Locations, 87 Locations; 135 Analysts Locations SOC analysts analysts SOC Analysts SOC analysts SOC Analysts Common name & Managed NGFW Compliance-as-a- Managed Threat Cloudflare for Managed NordLayer: VPN, Cloud Anti-DDoS On- - Packages description of w/ Secure SD- Service (CaaS): Detection and Applications Detection and SASE, ZTNA Demand
provider's most WAN build ongoing Response: EDR/ (Enterprise): Response NordPass: Cloud Email Security commonly sold SIEM, EDR & program to move MDR and/or SIEM CDN, DDoS password Managed Firewall products & Vulnerability beyond checkbox Security Testing: Mitigation, Digital Forensics management Managed Cloud services. Management compliance and pen test, network DNS, SSL, WAF and Incident NordLocker: WAAF Email Security & strengthen security, database Cloudflare Zero Response data encryption SASE O365 Backup security posture; security Trust Platform: supports common Proactive Threat Access (zero Managed Risk frameworks Hunting: trust), Gateway and Vulnerability including: CCPA, SpiderLabs (web filtering), FedRAMP, GDPR, experts Remote HIPAA, HITRUST Digital Forensics Browser CSF, ISO, ITIL, PCI, and Incident Isolation, SOC 1/2 Response: CASB, Email consulting Security services Cloudflare for Incident Response Infrastructure: Retainer: rapid Magic Transit access, bucket of (L3 DDoS hours Protection, Firewall-as-a- service, WAN- as-a-service) Cloudflare for Developers: serverless code deployment Risk & may include risk n/a in-house In-house n/a In-house NIST, n/a Third-party In-house Compliance assessments assessments: CSF, ISO assessments Assessments and gap GDPR, HIPAA, 27001/27002, for various analyses to HITRUST, ISO, CIS, GDPR, SEC, standards evaluate NIST, PCI, SOC HIPAA security posture, 1/2 assessments to determine compliance Penetration can be offered n/a Third-party (CBI In-house n/a In-house external, n/a Third-party n/a Test for Secure) internal, web app, infrastructure/ and social network, apps engineering/ (web/mobile), phishing devices Vulnerability tool to assess CODA Tenable.io, one- one-time or n/a ongoing n/a one-time or ongoing Tenable, Scanning computers, time or ongoing ongoing, Qualys, ongoing networks or Rapid7, Tenable.io applications for known weaknesses Security one-time n/a ICB (sold with offered standalone n/a n/a n/a offered standalone n/a
Workshop engagement compliance as-a- (NRC) with IT/Security service) staff and primary stakeholders to discuss their cybersecurity strategy and means of improvement End User one-time or n/a Cofense PhishMe, n/a n/a offered n/a n/a KnowBe4, Training ongoing LMS standalone Symbol cybersecurity Security (min. awareness 500 users) training offered directly to end users Email Security Secure Email FortiMail Mimecast MailMarshal proprietary n/a n/a offered standalone Mimecast (sold Gateway or as add-on) other product meant to detect malicious or fraudulent email content SIEM & Log a managed FortiSIEM Hosted Hosted: Fusion n/a Microsoft n/a offered standalone FortiSIEM Management solution that LogRhythm (logs (proprietary, Sentinel, Sumo (roadmap 2023) provides holistic must be ingested Microsoft Logic view of into Ntirety Sentinel) or On- customer’s environment; will Prem (Splunk, environment and not manage QRadar, correlates existing) LogRhythm); min. various data $25K MRC sources to identify threats in real time Managed combination of FortiEDR Palo Alto XDR Carbon Black, n/a Carbon Black n/a offered standalone FortiSIEM + Detection & security tools Microsoft (min. 50 (roadmap 2024) FortiEDR, Response and SOC Defender, Palo endpoints); SentinelOne (MDR) analysts used to Alto, SentinelOne; CrowdStrike, identify threats min. 250 seats Microsoft and respond to Defender (min. 25 incidents within endpoints); a customer SentinelOne environment Endpoint remote FortiEDR Palo Alto XDR n/a n/a Carbon Black NordLayer offered standalone FortiEDR, Protection management of (sold as add-on) (min. 50 FWaaS (min. 300 SentinelOne specified endpoints); (roadmap) endpoints) product CrowdStrike,
Microsoft Defender (min. 25 endpoints); SentinelOne WAF Web Application n/a Cloudflare, Prisma n/a cloud-based n/a n/a offered standalone n/a Firewall used to Cloud, ThreatX proprietary protect against WAF attacks targeting Internet-facing applications DDoS Solution n/a Prisma Cloud, n/a cloud-based, n/a n/a offered standalone n/a Mitigation designed to ThreatX circuit agnostic block Layer 3, 4, and Distributed 7 DDoS Denial of Service mitigation attacks from taking down a network or online application; especially relevant for companies who do business online Identity & a technique to n/a MFA: Duo, n/a proprietary n/a NordLayer sold as add-on Microsoft Access regulate who Microsoft, Ping; (SSO/MFA) Management can use CASB: Proofpoint (IAM) resources on a network; may include Single Sign-On, Cloud Access Security Broker, and Multi-Factor Authentication Perimeter a broad Fortinet Fortinet, Palo Alto offered standalone proprietary n/a NordLayer offered standalone Fortinet, Meraki Security approach to fortify the boundaries of a network; may include on-prem firewall, cloud firewall/VPN, intrusion detection, and intrusion prevention
Incident an organized, n/a provided via third offered standalone n/a Available for on- n/a offered standalone retainer Response forensic party demand 24/7 (roadmap 2023) approach to Incident investigate and Response or remediate a Emergency security breach; Incident can be on- Response. demand or via monthly retainer Virtual CISO an outsourced n/a offered offered standalone n/a offered n/a n/a offered CISO to help a standalone standalone standalone company build and maintain an information security program without an FTE; especially relevant to align with compliance standards
